Security and Compliance
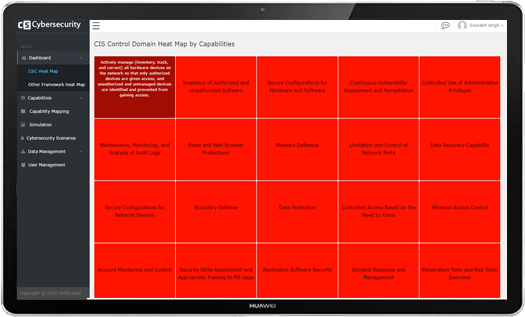
Cybersecurity Review provides the Customer with a foundational analysis of their Cybersecurity infrastructure taking into consideration current software deployment, usage and licensing data. The analysis will be the basis for the evaluation of the Customer’s basic Cybersecurity state, providing insights to what software is deployed and areas of potential risk.
Capabilities
Manage information security with automated user authentication to optimize security and for effective content management.
Authenticated Service
AD authentication to access all portals and their services, No data leakage or mapping of content with other providers.
Secured Configurational settings
Track cloud configurations with the customized baseline or recommendations for each individual resource.
Log Intelligence
Track and maintain log mechanisms with the help of CloudSupervisor®’s matured log tracking to track the new users and application behaviors around the virtual environments.
Compliance Management
Detailed reporting for any drift with the baseline values for the Governance & Regulatory Compliance (GRC) settings, maintained by CloudSupervisor®
Track Malicious activities
Any disorder with the regular usage of services is tracked and monitored to provide a thorough security around the inventoried applications.
Encrypted information
Exchange of sensitive information throughout the applications is encrypted to provide security and protection.





 CloudRecon
CloudRecon CloudSupervisor
CloudSupervisor